RAINBOW TABLES
I will discuss only about LM (LANMAN HASH) RAINBOW TABLE. Wikipedia defines Rainbow tables as
"A rainbow table is a lookup table offering a time-memory tradeoff used in recovering the plaintext password from a password hash generated by a hash function, often a cryptographic hash function. A common application is to make attacks against hashed passwords feasible. A salt is often employed with hashed passwords to make this attack more difficult, often infeasible"
At
they have defined Rainbow Table as....
decrypting of an encrypted element or object that contains the desired information. For discussion in this site, cracking is most closely related to the discovery of the password from an algorithmic hash based on a known encryption method. Typical encryption methods include, but are not limited to the following:
What are Rainbow Tables?
In simple terms, passwords stored in computers are changed from their plain text form to an encrypted value. This value or hash is the result of an algorithmic calculation designed for the operating system to use, but not to be plainly visible or intelligible to users. Let’s look at an example password and some associated hashes.
The password “rainbow” would look something like this if it were “Hashed” or encrypted with the following hashing selections:
Type
Hash
------------------
MD2
A8FA298E39DCCD4BB995 46AD015F4146
MD4
725C086015707D08849C C22283ADE154
MD5
CD13B6A6AF66FB774FAA 589A9D18F906
SHA-1
1EB08C4E3F8A5AB57617 23B1210AD4C30E41DC7
RIPEMD-160
4870CE7A5BB385EDC579 30F05E3DAB0FB883DCC4
LM
9224FC255C58C50E
NT
87F65D137998A4CE59EA 65B114A0F831
MySQL
32356F306146F12605E
MySQLSHA1
79239E0207CD5F6A472C 8795C73B451D349C8573
Cisco PIX
EQRTXAW3PX3q9K5A
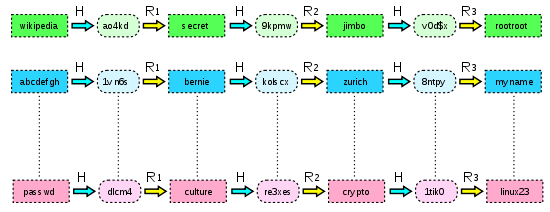
As you can see, the resulting information is quite useless to you and me. However, if there was a way to utilize an application to generate every possible combination of hash variation and then be able to compare your hash with all of those possibilities, you would have Rainbow Tables. The value of utilizing rainbow tables for password cracking and auditing is that traditional methods such as brute forcing and dictionary attacks are time consuming and inefficient. In many cases, the dictionary cracking method requires an enormous list(s) to be effective. One gigabyte of dictionary passwords might be able to yield a 40 to 50 percent compromise of a set of hashes. The same set of hashes with a complete set of Rainbow Tables properly implemented and utilized could effectively compromise 90 to 95 percent of the hashes in less than 25% of the time.
for AMAZING details PLEASE do visit
I will discuss only about LM (LANMAN HASH) RAINBOW TABLE. Wikipedia defines Rainbow tables as
"A rainbow table is a lookup table offering a time-memory tradeoff used in recovering the plaintext password from a password hash generated by a hash function, often a cryptographic hash function. A common application is to make attacks against hashed passwords feasible. A salt is often employed with hashed passwords to make this attack more difficult, often infeasible"

At
Code:
[B][COLOR=RoyalBlue][B]http://www.rainbowtables.net/tutorials.php
[/B][/COLOR][/B]they have defined Rainbow Table as....
decrypting of an encrypted element or object that contains the desired information. For discussion in this site, cracking is most closely related to the discovery of the password from an algorithmic hash based on a known encryption method. Typical encryption methods include, but are not limited to the following:
[*] LM and NTLM
[*] MD (Message Digest) 2, 4, and 5
[*] Cisco PIX password encryption
[*] MySQL, MySQL323, SHA1, ripemd160
What are Rainbow Tables?
In simple terms, passwords stored in computers are changed from their plain text form to an encrypted value. This value or hash is the result of an algorithmic calculation designed for the operating system to use, but not to be plainly visible or intelligible to users. Let’s look at an example password and some associated hashes.
The password “rainbow” would look something like this if it were “Hashed” or encrypted with the following hashing selections:
Type
Hash
------------------
MD2
A8FA298E39DCCD4BB995 46AD015F4146
MD4
725C086015707D08849C C22283ADE154
MD5
CD13B6A6AF66FB774FAA 589A9D18F906
SHA-1
1EB08C4E3F8A5AB57617 23B1210AD4C30E41DC7
RIPEMD-160
4870CE7A5BB385EDC579 30F05E3DAB0FB883DCC4
LM
9224FC255C58C50E
NT
87F65D137998A4CE59EA 65B114A0F831
MySQL
32356F306146F12605E
MySQLSHA1
79239E0207CD5F6A472C 8795C73B451D349C8573
Cisco PIX
EQRTXAW3PX3q9K5A
As you can see, the resulting information is quite useless to you and me. However, if there was a way to utilize an application to generate every possible combination of hash variation and then be able to compare your hash with all of those possibilities, you would have Rainbow Tables. The value of utilizing rainbow tables for password cracking and auditing is that traditional methods such as brute forcing and dictionary attacks are time consuming and inefficient. In many cases, the dictionary cracking method requires an enormous list(s) to be effective. One gigabyte of dictionary passwords might be able to yield a 40 to 50 percent compromise of a set of hashes. The same set of hashes with a complete set of Rainbow Tables properly implemented and utilized could effectively compromise 90 to 95 percent of the hashes in less than 25% of the time.
for AMAZING details PLEASE do visit
Code:
[B][COLOR=RoyalBlue][B]http://www.rainbowtables.net/index.php
[/B][/COLOR][/B]
